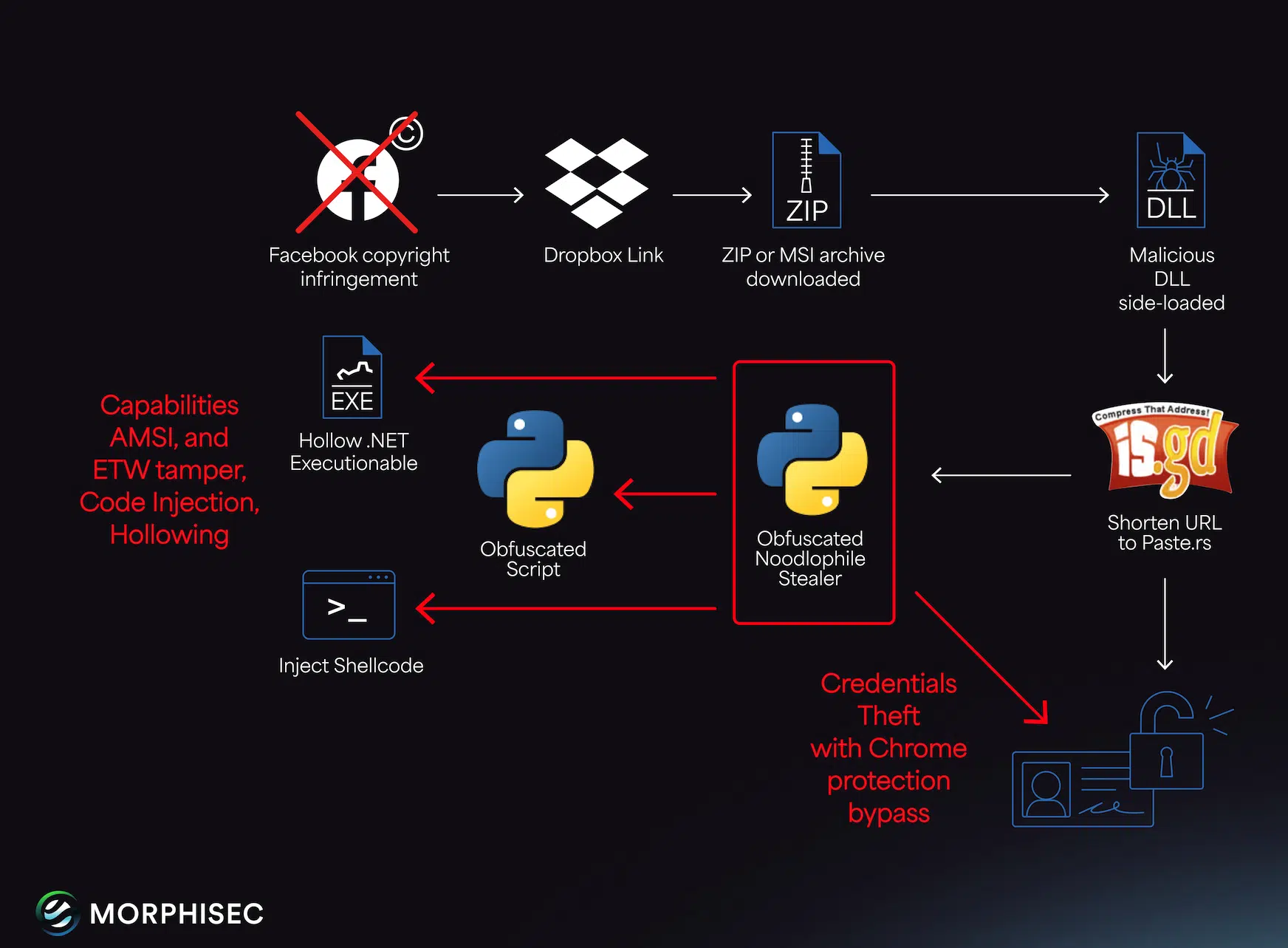
Okta open-sources Auth0 rules catalog for threat detection
Okta has open-sourced ready-made Sigma-based queries for Auth0 customers to detect account takeovers, misconfigurations, and suspicious behavior in event logs. Auth0 is Okta’s identity and access management (IAM) platform used by organizations for login, authentication, and user management services. By releasingg the detection rules, the companyaims to help security teams quickly analyze Auth0 logs for … Ler mais