Phishing Campaign Uses UpCrypter to Deploy Remote Access Tools
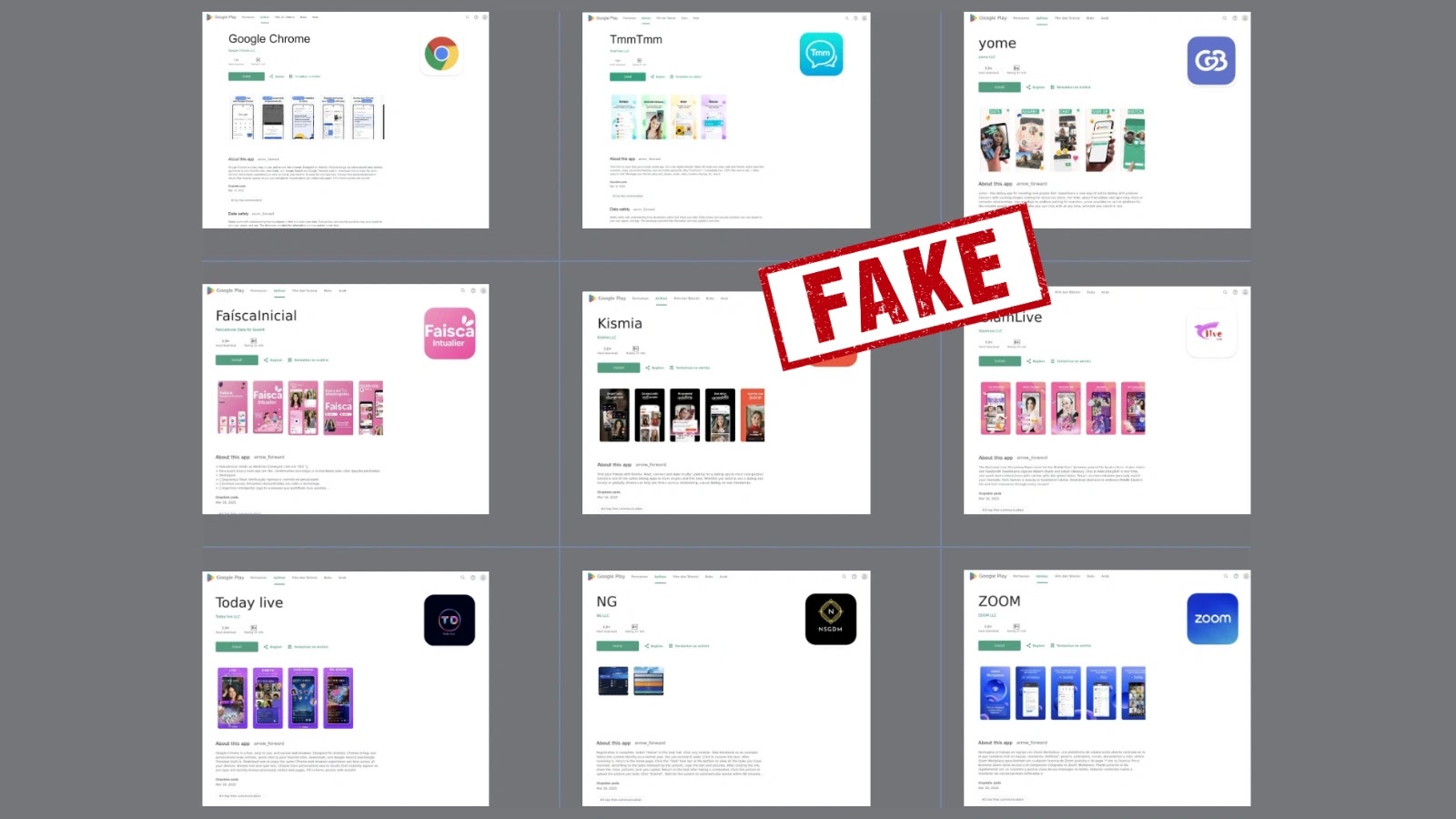
A global phishing campaign using personalized emails and fake websites to deliver malicious downloads has been identified by cybersecurity researchers. According to a new advisory by FortiGuard Labs, the operation employs a custom loader called UpCrypter to install a range of remote access tools (RATs), giving attackers prolonged control of compromised systems. How the Attack … Ler mais