Malicious apps with +19M installs removed from Google Play because spreading Anatsa banking trojan and other malware
Experts found 77 malicious Android apps with 19M+ installs on Google Play, spreading malware, including the Anatsa (TeaBot) banking trojan.
While investigating Anatsa (Tea Bot) banking trojan infections, Zscaler’s ThreatLabsdiscovered seventy-seven malicious Android apps with more than 19 million installs. Several Anatsa decoy apps have each been downloaded more than 50,000 times. The malicious apps were delivering multiple malware families toGoogle Play users.
“Alongside Anatsa, ThreatLabz identified and reported 77 malicious apps from various malware families to Google, collectively accounting for over 19 million installs.” reads the report published by ZScaler
Anatsa, a banking trojan first seen in 2020, has evolved into a major threat. The latest variant now targets more than 831 financial institutions worldwide, including banks, fintech services, and even cryptocurrency platforms, expanding its reach to countries like Germany and South Korea. Unlike earlier versions, it no longer relies on dynamic code loading but directly installs its payload, making infections faster and harder to stop. It also uses DES encryption and device-specific restrictions to avoid detection.
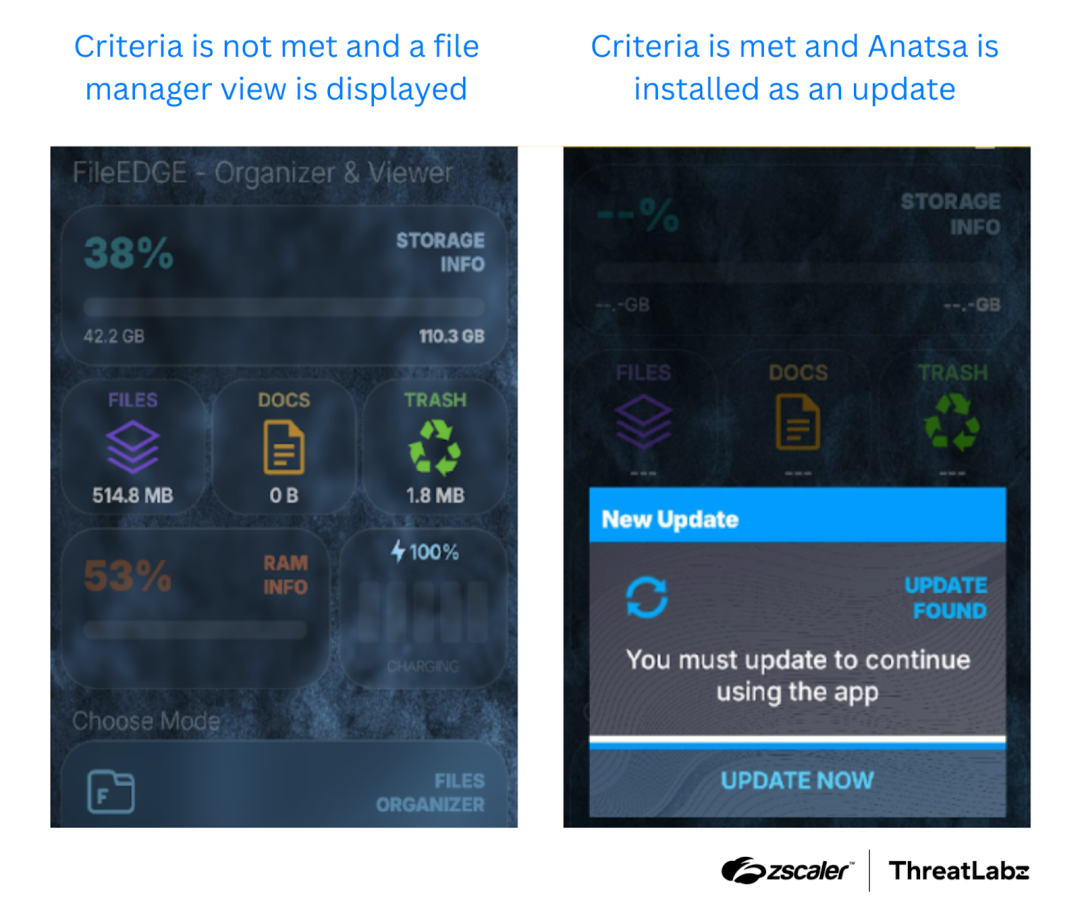
“Unlike in previous campaigns, the latest Anatsa campaigns implement various anti-analysis techniques. The parent installer now decrypts each string at runtime using a dynamically generated Data Encryption Standard (DES) key, making it more resistant to static analysis tools. Furthermore, Anatsa has enhanced its evasion strategies by performing emulation checks and verifying device models to bypass dynamic analysis environments.” continues the report. “After confirming that the C2 server is active and the device meets the necessary criteria, the installer proceeds to download Anatsa as an update. If these conditions are not met, the application displays a file manager view to the user, maintaining the appearance of a legitimate application, as shown in the figure below.”
Anatsa employs advanced evasion by periodically changing package names and hashes, using APK ZIP obfuscation, and hiding DEX payloads in malformed archives that bypass static analysis. The malware requests accessibility permissions to auto-enable dangerous privileges, then establishes XOR-encrypted C2 communication. The malicious code captures banking credentials through fake login pages tailored to detected apps. Anatsa currently targets 831 financial apps, though many injection templates remain incomplete.
ThreatLabz reports a surge in adware and malware like Joker, Harly, and Anatsa on Google Play, while Facestealer and Coper show a sharp decline.
“Anatsa continues to evolve and improve with anti-analysis techniques to better evade detection. The malware has also added support for more than 150 new financial applications to target.” concludes the report. “Our research demonstrates the techniques that Anatsa and other Android malware families leverage for distribution through the official Google Play Store. Android users should always verify the permissions that applications request, and ensure that they align with the intended functionality of the application.”
Follow me on Twitter:@securityaffairsandFacebookandMastodon
(SecurityAffairs–hacking,Google Play)