More than 28,200 Citrix instances are vulnerable to a critical remote code execution vulnerability tracked as CVE-2025-7775 that is already being exploited in the wild.
The vulnerability affectsNetScaler ADC and NetScaler Gateway and the vendor addressed it in updates released yesterday.
According to the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and Citrix, the security issue has been exploited as a zero-day vulnerability.
The versions affected by CVE-2025-7775 are 14.1 before 14.1-47.48, 13.1 before13.1-59.22, 13.1-FIPS/NDcPP before 13.1-37.241-FIPS/NDcPP, and 12.1-FIPS/NDcPP up to12.1-55.330-FIPS/NDcPP.
Citrix does not provide any mitigations or workarounds and urgesadmins to upgrade the firmware immediately.
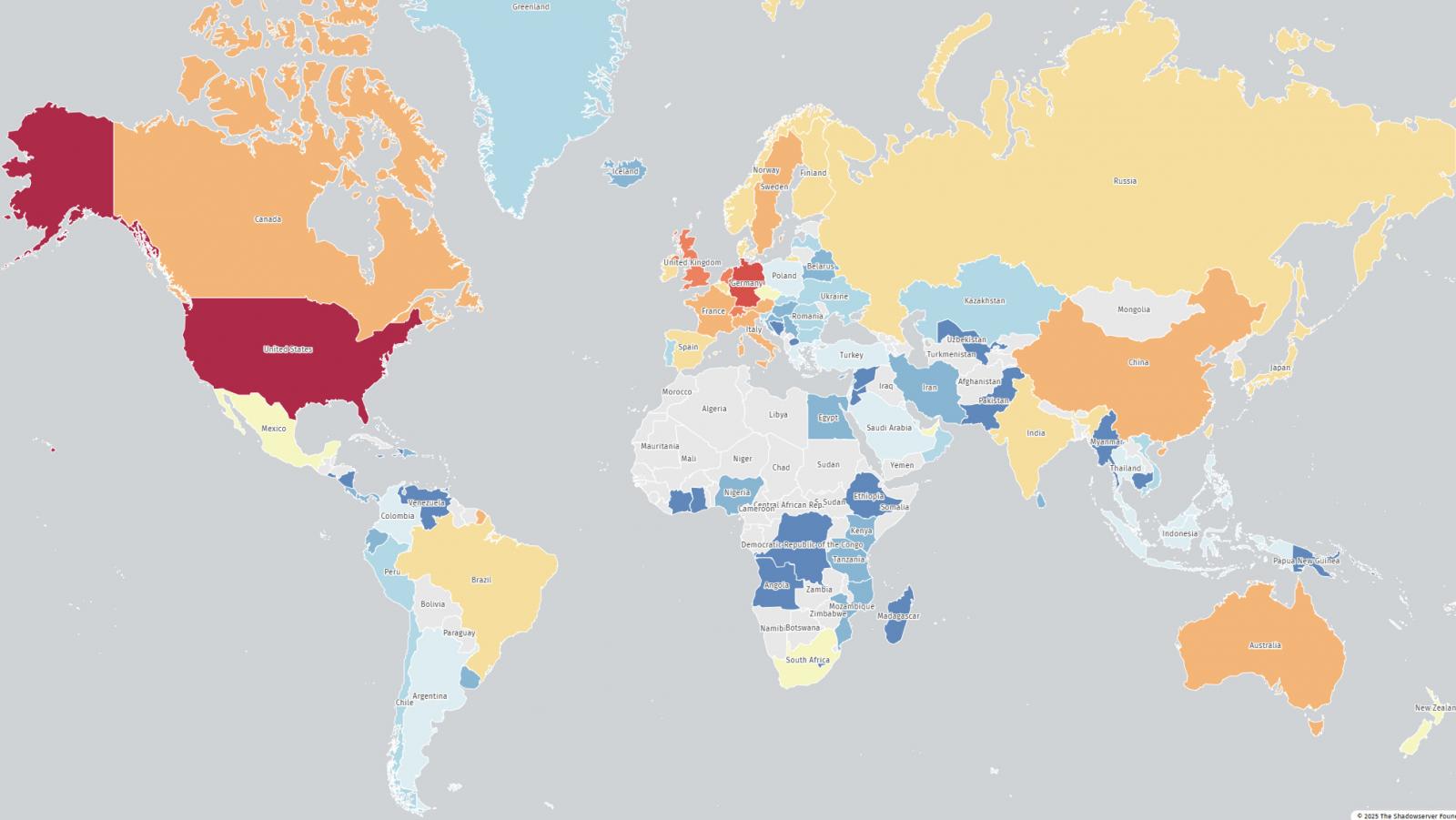
Internet scans conducted by the threat monitoring platform The Shadowserver Foundationsoon after the flaw was disclosedshow that there weremore than 28,000 Citrix instancesvulnerable to CVE-2025-7775.
Most of the vulnerable instances are located in the United States (10,100), followed by Germany (4,300), the United Kingdom (1,400), the Netherlands (1,300), Switzerland (1,300), Australia (880), Canada (820), and France (600).