Over 800 N-able N-central servers remain unpatched against a pair of critical security vulnerabilities tagged as actively exploited last week.
N-central is a popular platform used by many managed services providers (MSPs) and IT departments to monitor and manage networks and devices from a centralized web-based console.
Tracked as CVE-2025-8875 and CVE-2025-8876, the two flaws can let authenticated attackers to inject commands due to improper sanitization of user input and execute commands on unpatched devices by exploiting an insecure deserialization weakness, respectively.
N-able has patched them in N-central 2025.3.1 and told BleepingComputer on Thursday that the security bugs are now under active exploitation, urging admins to secure their servers before further information on the bugs is released.
“Our security investigations have shown evidence of this type of exploitation in a limited number of on-premises environments. We have not seen any evidence of exploitation within N-able hosted cloud environments,” N-able told BleepingComputer.
“You must upgrade your on-premises N-central to 2025.3.1. (Details of the CVEs will be published three weeks after the release as per our security practices.),” N-able added in a Wednesday advisory.
On Friday, the internet security nonprofit Shadowserver Foundation is tracking 880 N-central servers that are still vulnerable to attacks exploiting the two vulnerabilities, most of them located in the United States, Canada, and the Netherlands.
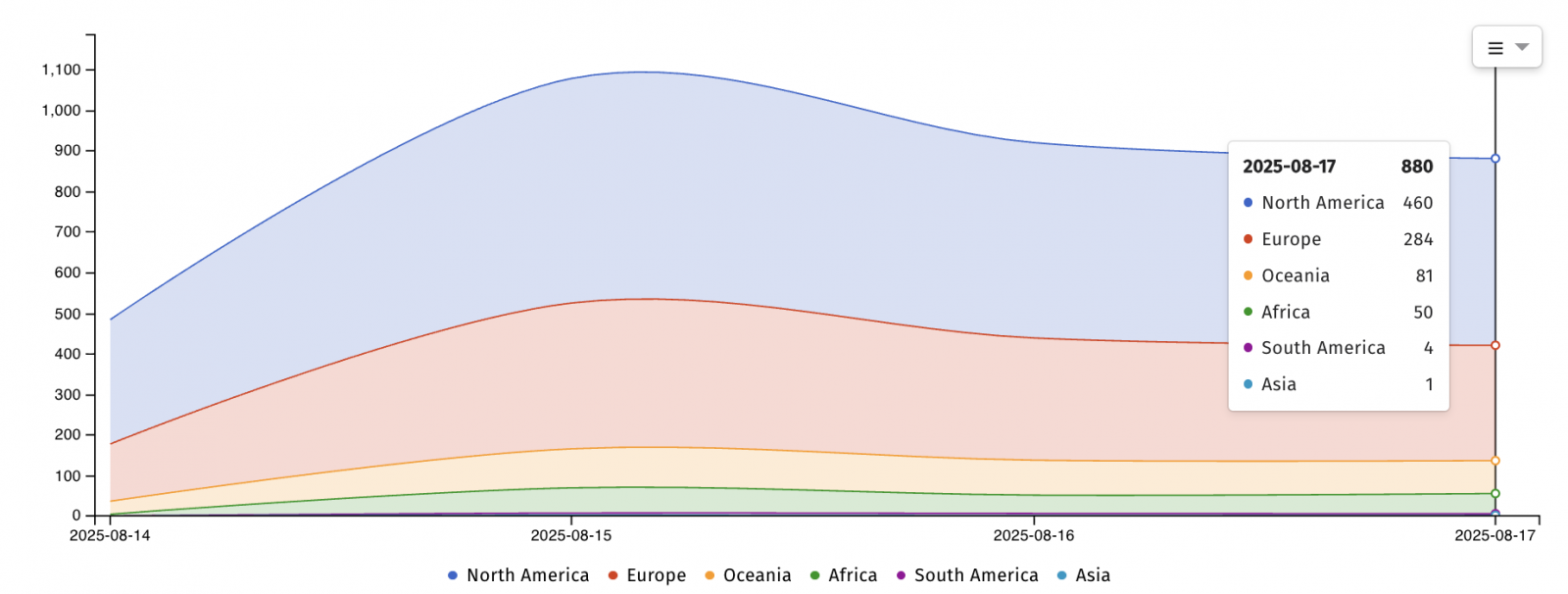
In total, approximately 2,000 N-central instances are currently exposed online, according to Shodan searches.
Federal agencies ordered to mitigate within a week
CISA has also added the flaws to its Known Exploited Vulnerabilities Catalog, tagging them as exploited in zero-day attacks one day before N-able confirmed the flaws are being abused in the wild.
The U.S. cybersecurity agency ordered all Federal Civilian Executive Branch (FCEB) agencies, including the Department of Homeland Security, the Department of the Treasury, and the Department of Energy, to patch their systems within one week, by August 20, as mandated by the November 2021 Binding Operational Directive (BOD) 22-01.
Although non-government organizations are not required to take action, as BOD 22-01 primarily targets U.S. federal agencies, CISA urged all network defenders to secure their systems against ongoing attacks.
“Apply mitigations per vendor instructions, follow applicable BOD 22-01 guidance for cloud services, or discontinue use of the product if mitigations are unavailable,” CISA said.
“These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise.”


