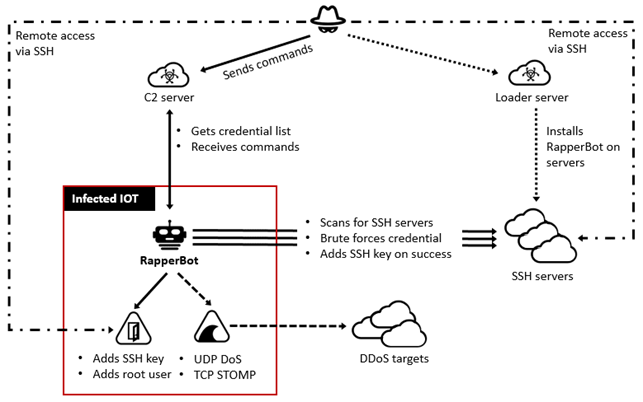
Os atores de ameaças são representados como suporte do Google para farejar suas credenciais de login
Os atores de ameaças estão se apresentando como agentes de suporte do Google em um número crescente de ataques complexos de engenharia social, a fim de aproveitar as ferramentas de recuperação de contas e obter credenciais do usuário sem autorização. Essas campanhas aproveitam os canais de comunicação de aparência legítima, como números de telefone falsificados … Ler mais