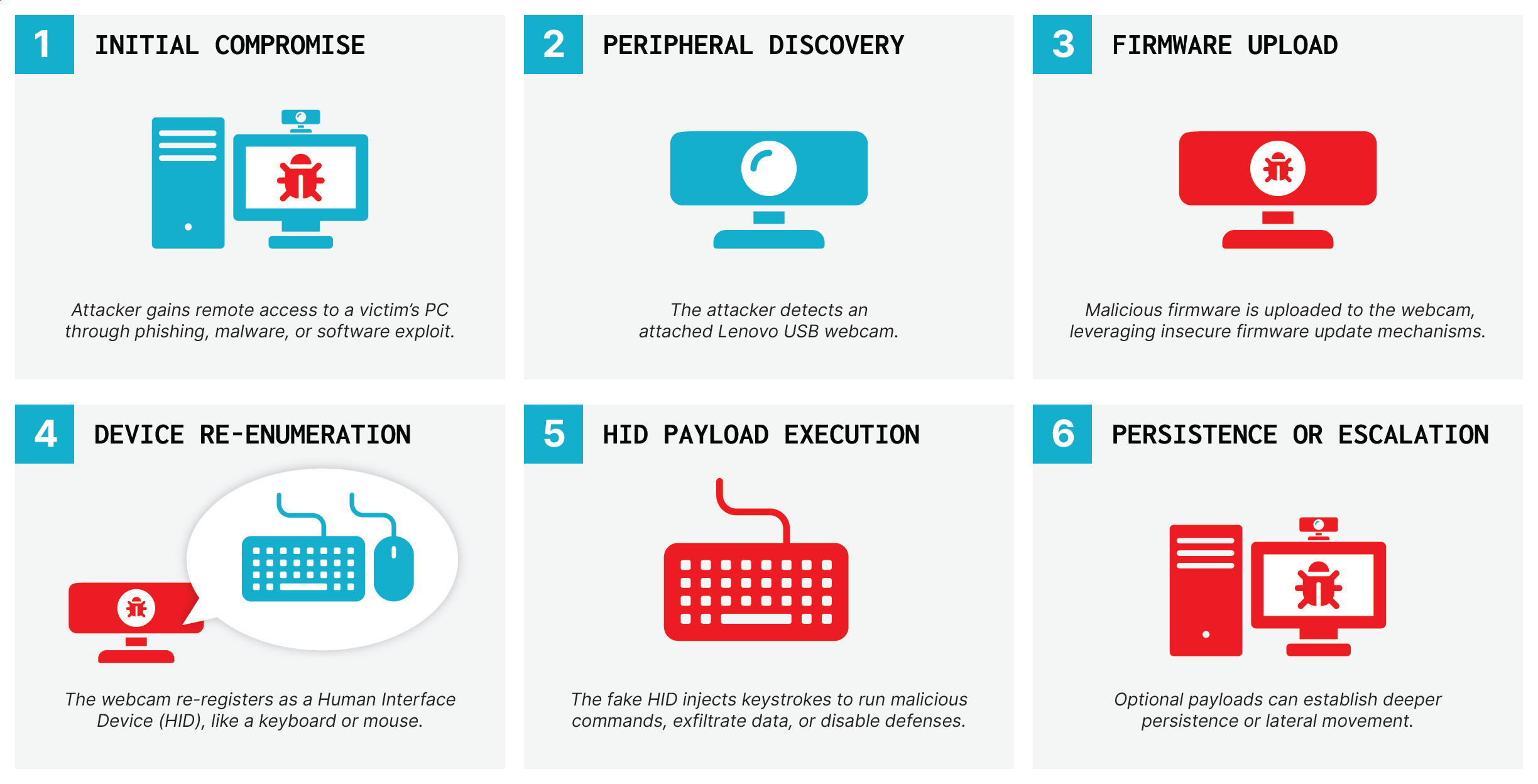
FBI warns of Russian hackers exploiting 7-year-old Cisco flaw
The Federal Bureau of Investigation (FBI) has warned that hackers linked to Russia’s Federal Security Service (FSB) are targeting critical infrastructure organizations in attacks exploiting a 7-year-old vulnerability in Cisco devices. The FBI’s public service announcement states that the state-backed hacking group, linked to the FSB’s Center 16 unit and tracked as Berserk Bear (also … Ler mais