Microsoft warns that a threat actor tracked as Storm-0501 has evolved its operations, shifting away from encrypting devices with ransomware to focusing on cloud-based encryption, data theft, and extortion.
The hackers now abusenative cloud features to exfiltrate data, wipe backups, and destroy storage accounts, thereby applying pressure and extorting victims without deploying traditional ransomware encryption tools.
Storm-0501 is a threat actor who has been active since at least 2021, deploying the Sabbath ransomware in attacks against organizations worldwide. Over time, the threat actorjoined various ransomware-as-a-service (RaaS) platforms, where they usedencryptors from Hive, BlackCat (ALPHV), Hunters International, LockBit, and, more recently, Embargo ransomware.
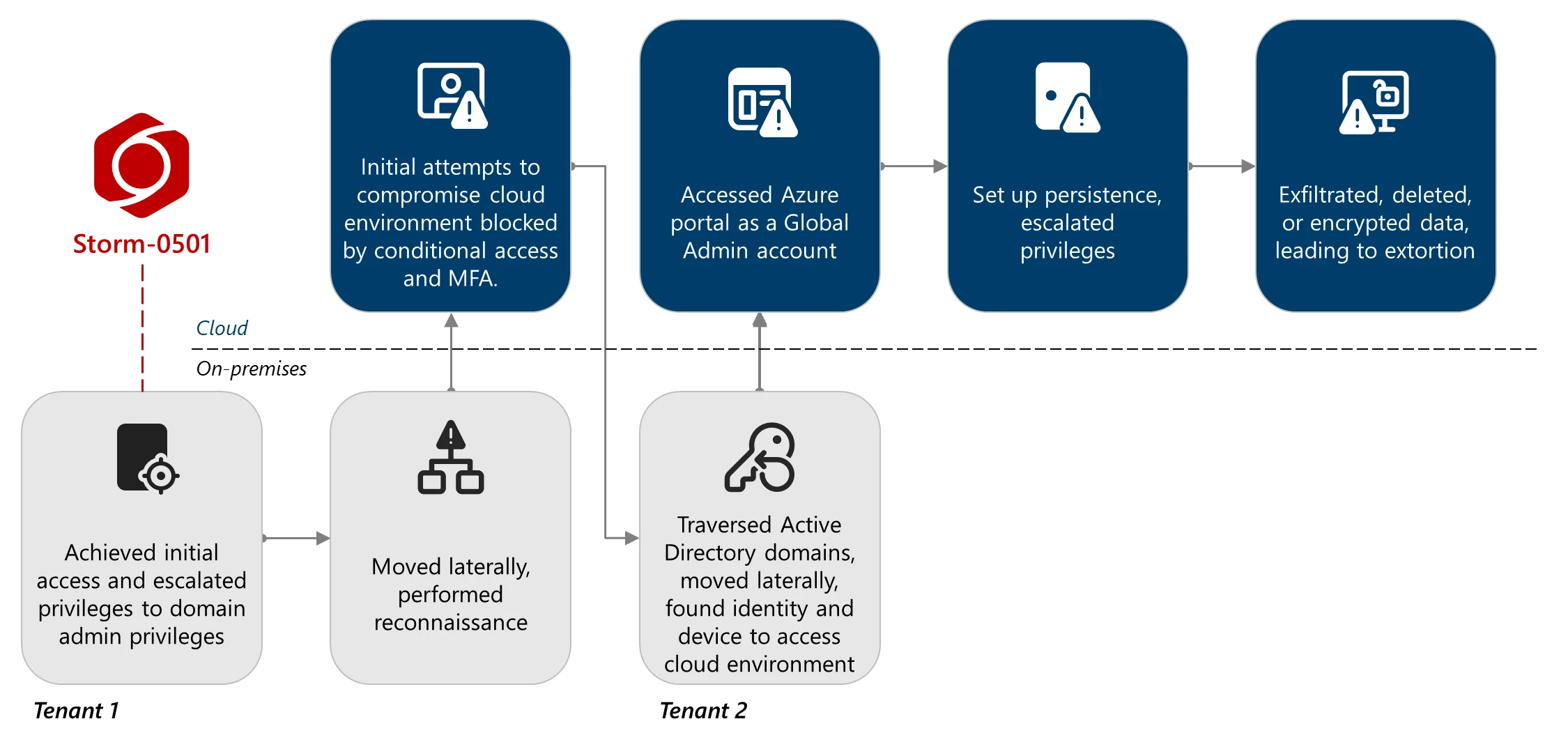
In September 2024, Microsoft detailed how Storm-0501 extended its operations into hybrid cloud environments, pivoting from compromising Active Directory to Entra ID tenants. During these attacks, the threat actors either created persistent backdoors through malicious federated domains or encrypted on-premises devices using ransomware, such as Embargo.
A new report by Microsoft today outlines a shift in tactics, withStorm-0501 no longer relying on on-premises encryption and instead conducting attacks purely in the cloud.
“Unlike traditional on-premises ransomware, where the threat actor typically deploys malware to encrypt critical files across endpoints within the compromised network and then negotiates for a decryption key, cloud-based ransomware introduces a fundamental shift,” reads the report by Microsoft Threat Intelligence.
“Leveraging cloud-native capabilities, Storm-0501 rapidly exfiltrates large volumes of data, destroys data and backups within the victim environment, and demands ransom—all without relying on traditional malware deployment.”
Cloud-based ransomware attacks
In recent attacks observed by Microsoft,the hackers compromised multiple Active Directory domains and Entra tenants by exploiting gaps in Microsoft Defender deployments.
Storm-0501 then used stolen Directory Synchronization Accounts (DSAs) to enumerate users, roles, and Azure resources with tools such as AzureHound. The attackers eventually discovered a Global Administrator account that lacked multifactor authentication, allowing them to reset its password and gain complete administrative control.
With these privileges, they established persistence by adding malicious federated domains under their control, enabling them to impersonate almost any user and bypass MFA protections in the domain.
Microsoft says they escalated their access further into Azure by abusing the Microsoft.Authorization/elevateAccess/action, which allowed them to ultimately assign themselves to Owner roles, effectively taking over the victim’s entire Azure environment.